Introduction:
Creating SSH keys for your Ubuntu 18.04 server can enhance the security of your server by making plaintext password logins redundant. OpenSSH is a free and open source client/server technology for secure remote login. OpenSSH is into SSHD (server ssh service) and various connection protocols such as sftp, scp, ssh and more. You can remote login to your server by using a combination of passwordless private and public keys or password protect your key to decrypt the key. It is an alternative security method for user passwords. This method is recommended on a VPS, cloud, dedicated or even home-based server or laptop. This article shows how to set up SSH keys on Ubuntu 18.04 LTS server.
Steps in generating the SSH private and public key
- Generate the key pair using ssh-keygen
- Install the public SSH key
- Make a user as a sudo user
- Disable Root and Password login on SSHD
Generate the key pair using ssh-keygen
On the local Linux machine that you will be using to generate the ssh key we will need to create the .ssh directory and set the permissions for this file.
mkdir -p $HOME/.ssh
chmod 0700 $HOME/.ssh
Now let’s generate the key pair
chris@wos:~$ ssh-keygen
Generating public/private rsa key pair.
Enter file in which to save the key (/home/chris/.ssh/id_rsa):
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /home/chris/.ssh/id_rsa.
Your public key has been saved in /home/chris/.ssh/id_rsa.pub.
The key fingerprint is:
SHA256:8y81OU84qXCl5WkWgbFRCK5WmdcyCkuP5/l2B/yaM2E chris@wos
The key’s randomart image is:
+—[RSA 2048]—-+
| ..o=. |
| . oo+. |
| o = = .. |
| . B o o+ |
| = S * * |
| . o.+o E . |
| oo.* X |
| .+.+.+ |
| ..o+= |
+—-[SHA256]—–+
As we can see 2 files were generated:
Your identification has been saved in /home/chris/.ssh/id_rsa. <– This is your private key and should not be shared with anybody.
Your public key has been saved in /home/chris/.ssh/id_rsa.pub. <– This is your public key that is used to verify the private key.
We now need to transfer and install the public key onto the remote server. To do this we will use SSH and use the following command:
ssh-copy-id -i $HOME/.ssh/id_rsa.pub chris@134.209.204.2
For this guide we are going to be copying the id_rsa.pub file to a remote server with ip address 134.209.204.2 with username chris. Please amend this to your own IP address and username.
Now let’s test the SSH key by SSH to the server.
ssh chris@134.209.204.2
Passphrase for key “imported-openssh-key”:
Welcome to Ubuntu 18.04.2 LTS (GNU/Linux 4.15.0-45-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
I setup a passphrase for my key so I was requested to enter this as I attempted to login. If you set a passphrase then you should see one of the following inputs:
Passphrase for key “imported-openssh-key”:
Enter passphrase for key ‘/home/user/.ssh/id_rsa.pub
If you did not set a passphrase then you should login without the need of entering any passwords.
Make user sudo and disable root login on SSH
Before completing these steps we need to be logged in as root user. For this demonstration we will be adding user chris to the sudo group.
usermod -aG sudo chris
Now lets change from root to chris user to test that sudo is working properly
su chris
If done correctly you should see the following on the SSH client:
root@wp-site:~# su chris
To run a command as administrator (user “root”), use “sudo “.
See “man sudo_root” for details.
chris@wp-site:/root$
Now the user chris can run root commands with sudo. The next step is to now disable root login from SSHD. Let’s open the sshd_config file and make the required changes.
sudo nano /etc/ssh/sshd_config
This will ask you for your user password as we will be running this command with root privileges. We need to find and replace the following line:
Change PermitRootLogin yes to no
PermitRootLogin no
Finally let’s disable plaintext passwords being allowed on the server
Change PasswordAuthentication no to yes
PasswordAuthentication no
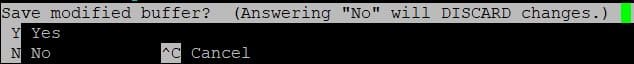
We need to save and exit NANO now so lets press the following keys:
CTRL + X Exit the application. You will be prompted if you would like to save the changes:
Now we need to restart the SSHD server for the new changes to take effect
chris@wp-site:/root$ service sshd restart
==== AUTHENTICATING FOR org.freedesktop.systemd1.manage-units ===
Authentication is required to restart ‘ssh.service’.
Authenticating as: ,,, (chris)
Password:
==== AUTHENTICATION COMPLETE ===
Now you will not be able to log onto your SSH server with a standard password or as root user. This completes this guide and don’t forget if you have any questions then just write a comment below or contact us for a more personal guide.